
Security compliance
Ensure your information security with RELEX
While no connected system is completely secure, our comprehensive security approach protects against external threats by making attacks harder to execute and faster to detect. We address all potential vulnerabilities since attackers often exploit multiple weaknesses to cause disruptions, steal data, or deploy ransomware. Our enterprise-grade security eliminates weak spots that could put your business at risk.
Ensure your infosec with our end-to-end security system framework
RELEX mitigates risk from external threats with a comprehensive security system covering all aspects of information security. With this framework we protect your data and ensure there is no disruption to your business. It is critical to have all parts completely covered through a robust enterprise-grade security approach, because the weakest link will be the most likely target.
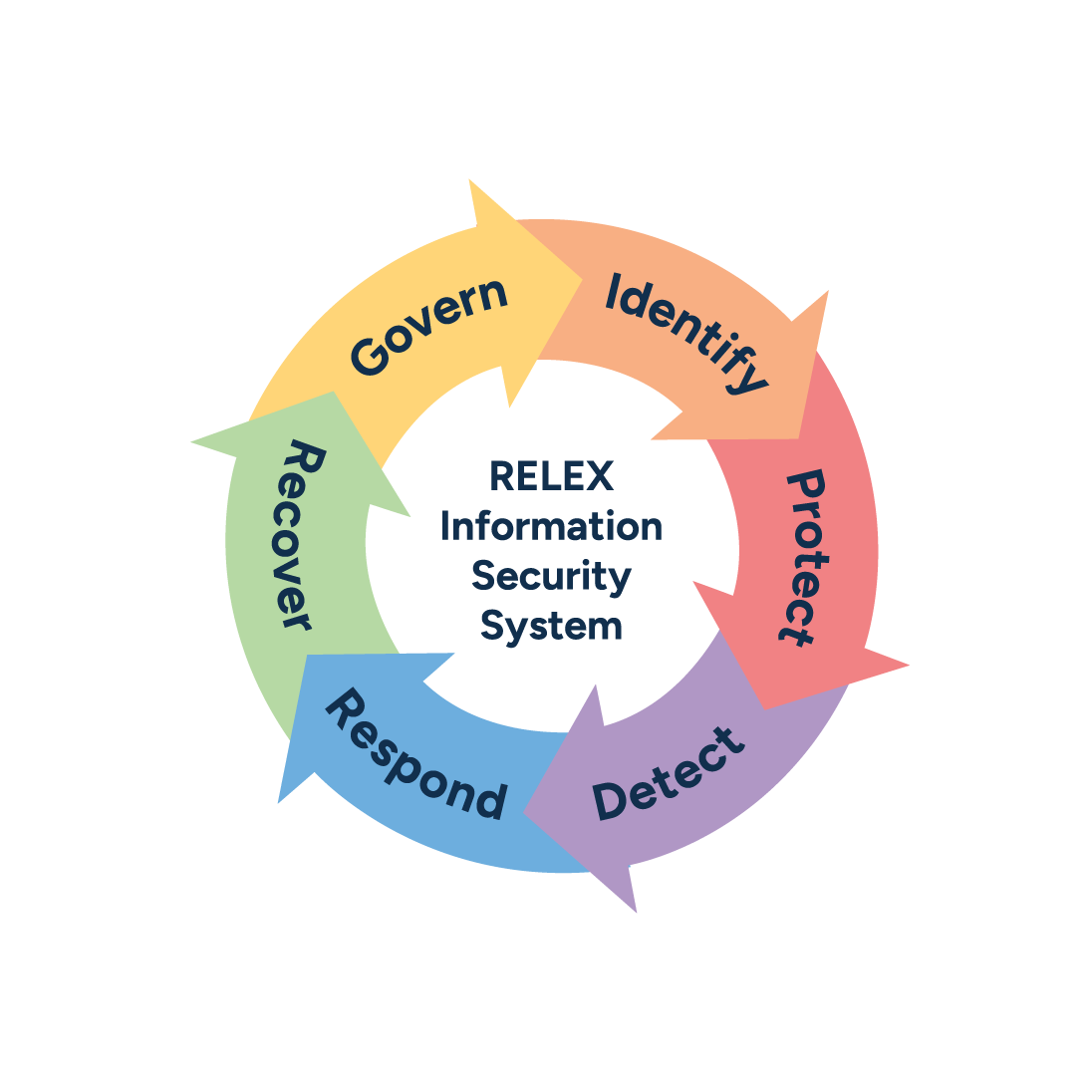
The RELEX security framework
Identify
We carry out continuous identification of threats in a changing landscape to ensure protection against any potential new risk.
- Secure software development practices
- Threat modelling and security inspections for new software
- Automated vulnerability scanning of software components
- Regular penetration testing

Protect
We have implemented protection mechanisms on all levels of operations.
- Access control to prevent only authorized access to systems
- Network-level security mechanisms such as segmentation and policies
- Authenticated and encrypted data transfers
- Frequent security patches
- All RELEX personnel undergo mandatory security training periodically

Detect
We perform continuous automated security monitoring, detection and analysis.
- 24/7 Security Operations Center acting on the first indications of suspicious activity
- Early intervention reduces the impact of incidents

Respond
We have established and efficient incident management processes.
- If incidents arise quick action can be taken with clear responsibilities and roles to contain the issues, minimize impact, initiate recovery and communicate

Recover
We have put in place multiple overlapping recovery mechanisms to mitigate the risk of disruption to our customers’ businesses.
- System redundancy ensures uninterrupted service despite compromised processing resources
- Backups are taken as snapshots in time and stored offsite in Microsoft Azure for no longer than necessary. There are regular disaster recovery tests to verify the backup restore process is working smoothly.

Govern
The main parties responsible for information security are the Chief Information Security Officer (CISO), information security team, and Information Security steering group.
- We are GDPR compliant in our governance and incident response procedures


ISO 27001
To gain ISO 27001:2013 certification for RELEX’s Inventory and Supply Chain software, we had to demonstrate a systematic and rigorous approach to managing sensitive information. An internationally respected independent auditor judged that our security processes met the highest standards for setting up, maintaining and continuously improving an information security management system.

SOC 2
The ISAE 3000 SOC 2 standard for assurance was originally developed by the American Institute of Certified Public Accountants and is widely regarded as the gold standard for reporting on information security. It requires that companies establish and follow strict standards and protocols for information security.
RELEX Inventory and Supply Chain software has been audited both for Type I and Type II reports. Whereas Type I is effectively a snapshot of security at a particular point in time, Type II is only issued after an organization’s information security has been operating effectively for a minimum of twelve months.

GDPR
The General Data Protection Regulation (GDPR) is a comprehensive data protection law that regulates the use of personal data of EU residents and provides individuals rights to exercise control over their data. For more information on how RELEX complies with Art. 13/14 of Regulation (EU) 2016/679 (General Data Protection Regulation), please see our privacy policy.
Ready to transform your supply chain & retail planning?
We’re happy to discuss your business needs and share how our market-leading, unified platform can help you drive profitable growth across your sales and distribution channels. Discover why top industry analysts position RELEX as Leaders in the market.